- Gheorghe Farcas, DevOps at BoatyardX
On one of our client’s projects, the developers needed a fast and secure way to access a mixed cluster of cloud and on-prem servers, and the client’s IT manager also requested detailed oversight. The task is to implement a user-friendly solution, preferably with a nice GUI (Graphical User Interface). It is time for the DevOPS to deliver.
Bringing everybody onboard, securely!
In this early stage, all the project’s servers were moved behind a Bastion server and access was granted via terminal-based access scripts.

Teleport – the “what”
So, what is Teleport ?
Teleport, is an open infrastructure access platform designed to provide secure access to cloud computing resources and on-premises infrastructure. The program was created by Gravitational, a company founded in 2015 with the goal of making it easier for businesses to manage and secure their IT infrastructure.
Teleport is a certificate authority and identity-aware, multi-protocol access proxy which implements protocols such as SSH, RDP, HTTPS, Kubernetes API, and a variety of SQL and NoSQL databases. It is completely transparent to client-side tools and designed to work with everything in today’s DevOps ecosystem.
The key concept of Teleport’s architecture is the cluster. A Teleport cluster consists of the Teleport Auth Service, Teleport Proxy Service, Teleport agents, and resources that you want to connect to such as Linux or Windows servers, databases, Kubernetes clusters, Windows desktops, and internal web apps.
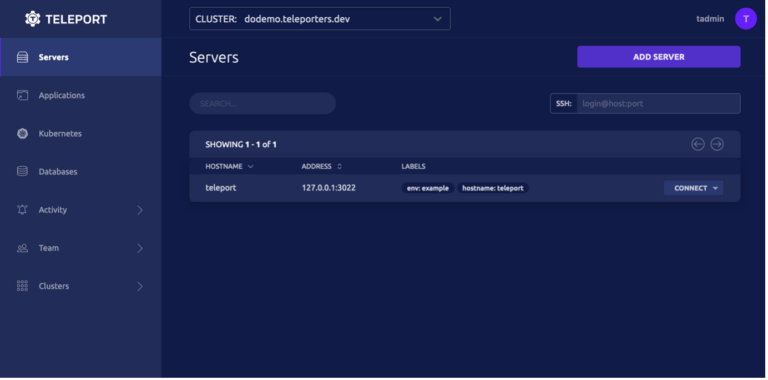
The Teleport web interface (image source https://goteleport.com/docs/try-out-teleport/digitalocean/)
From a high-level perspective, these are just some of the traits Teleport holds:
- It provides a unified access interface for managing user access.
- All the info on the resources administered via Teleport can be customized. This way, an admin can adapt the info to his needs.
- Accessing Teleport can be done securely, using MFA (Multi Factor Authentication), both via a GUI and via a Command Line Client (tsh). The GUI can be accessed either via a web browser, or by installing the Teleport Connect app, available for macOS, Linux and Windows.
- As administrators, in Teleport we can create “roles”. Roles govern access to databases, SSH servers, Kubernetes clusters, Windows desktops, and web apps. In Teleport, any local, SSO, or robot user can be assigned one or several roles.
- Once connected to a server in Teleport via the web browser or via the open-source Teleport Connect app, the user has direct access to a terminal window, in the browser or in the app.
- An Audit log captures all the activity on the estate. An admin can see who was where, when, and for how long. On top of that, everything that everybody does on the resources administered through Teleport can be recorded as a video. Admins have instant access to all the recordings. This comes in handy both security-wise and training-wise.
- Teleport has two tiers: the free tier called Community is great for testing and basic operations. There is also Teleport Enterprise which is a paid tier.

Teleport – the “how”
The foundation of Teleport’s architecture is the cluster. A Teleport cluster consists of the Teleport Services (Teleport Auth and Teleport Proxy), Teleport agents, and the resources that you want to connect to such as Linux or Windows servers, databases, Kubernetes clusters, Windows desktops, and internal web apps.
To create a minimal Teleport cluster, we need to launch three components:
- Teleport Auth Service. The certificate authority of the cluster. It issues certificates to clients and maintains the audit log.
- Teleport Proxy Service. The proxy allows access to cluster resources from the outside. Typically, it is the only service available from the public network.
- Teleport agents. A Teleport agent runs in the same network as a target resource and speaks its native protocol, such as the SSH, Kubernetes API, HTTPS, PostgreSQL, and MySQL wire protocols.
The clients must authenticate with Teleport and receive a client certificate, which automatically works for all the resources in a cluster. Also, the users and servers must all join the same cluster before access can be granted.
To join a cluster, both users and servers must authenticate and receive certificates.
The CA of the cluster is the Teleport Auth Service, which issues certificates for both users and servers with all supported protocols.
To sum it up, Teleport is quite easy to implement: we install a Teleport server, to which we add the users and the resources. Installing the clients is as simple as running a line of code generated by the server. We can access the server via a web-based client, or via tsh.
Teleport – the “why”
An image says a thousand words. We will go for the double of that:
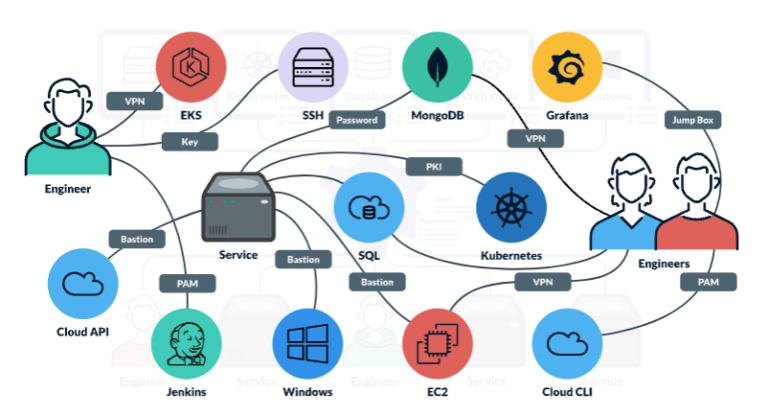
Before Teleport (image source https://goteleport.com/)
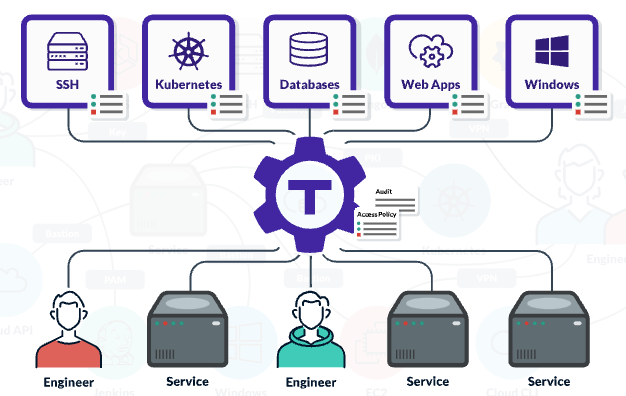
After Teleport (image source https://goteleport.com/)
Wrapping it up: to Teleport or not to Teleport?
We implemented Teleport on a few clusters of Linux servers, and it does what it claims to do.
The IT Manager has a clear overview of the entire estate, of the current access level of everyone, and all the activity is logged into video files that can be easily previewed.
Every instance’s console can be accessed via the web interface too, in a tabbed way, which is a definite plus.
The developers love it because they can use it in the terminal, via the “tsh” protocol of the app.
Using the Teleport platform for a few months now, we noticed one drawback, though: updates roll out often (one per week, as a loose average), so we must update the server and the clients accordingly, which can be a bit of a hassle sometimes. Other than that, the app (which is currently at version 13.3.4) is mature enough to be taken into serious consideration.
Read more tech topics
Building a cloud-based product can be daunting for startups, especially when faced with a plethora of choices, trade-offs, and challenges.
Proud of your product but sense it hasn’t quite hit its stride? UX audits are an essential tool to ensure it hits its full potential.
At Adminovate 2024, Karolina Coates, Head of Design at BoatyardX, joined industry leaders to discuss the evolving landscape of user experience (UX) and fintech innovation.
The BoatyardX DiscoverX workshop is a collaborative, interactive experience where clients have the opportunity to explore product and technology concepts.
In today's fast-paced digital landscape, businesses are continually seeking innovative solutions to manage their infrastructure efficiently – and for good reason.
Within the sphere of modern applications, prioritising user experience has become paramount.
Whether you are a startup or a large corporation, it's likely you will face many of the same challenges in building the first version of a new product or application. We explore some of the critical success factors and lessons learned from supporting a broad range of clients in bringing new products to life.
We live in the times when seamless user experiences (UI/UX) are the cornerstone of digital success, businesses are strategically leveraging the nearshore advantage to bolster their design teams.
Before solution and implementation are merged into the upstream branch, a code review is a crucial stage in the software development cycle to obtain a second viewpoint.
Computer vision has become a significant influence in the remaking of numerous sectors in a time when technological innovation is the driving force.
In today's rapidly evolving digital landscape, the success of a product or service hinges on the user experience (UX) it delivers.
With over four years of experience as a .NET developer under his belt, Petru felt it was time to explore the growing demand for DevOps expertise, specifically in technologies.
WebRTC (Web Real-Time Communication) is an open-source transformative technology that revolutionizes real-time audio, video, and data sharing within web browsers.
What do startup founders and enterprise technology leaders have in common? Nightmare stories about unintended consequences of technology decisions.
Cognitive biases can have a significant impact on the quality and effectiveness of software being developed. How can software developers mitigate this impact?
At a recent Microsoft event speakers and attendees struggled to best describe the significance of AI and its potential impact on enterprise.
More organisations are starting to realise that the cloud is a great enabler for innovation, not just a more efficient way of running IT applications and services.
Skill gaps, high employee turnover and fierce competition for limited talent have only added to the pressure that businesses are facing from inflation. Though it may seem counter intuitive, it’s actually a good time to modernise or even replace applications, because they could be compounding your skills challenges.
Meta has called 2023 ‘a year of efficiency’ and they are far from alone in the corporate world. Many businesses are knuckling down, shedding staff and focussing on the old adage of ‘doing more with less’. Belt tightening is a business initiative again, like the bad old days of 2008.
Factors to consider when deciding whether or not to automate your QA.
At close to 4 years old BoatyardX has, for most of its short life, been a remote-first organisation.
How design helps you validate your product ideas within our Discovery Framework.
Have you ever wondered what it takes to have that genius spark that leads to groundbreaking, brilliant ideas?
This article briefly highlights the challenges faced by many software companies, and elements of the solutions we’ve helped map out with them.
This article briefly highlights the challenges faced by many software companies, and elements of the solutions we’ve helped map out with them.
De-risk your product build by answering fundamental product and technology questions up front
Often entrepreneurs skip brand development because of budget limitations or lack of available skillset. A solid brand strategy is, however, the foundation of a successful venture which stands out from the crowd.
An active player on the IT scene, BoatyardX was featured by Today Software Magazine (RO) in tech related topics as a subject matter expert.
When technology isn’t your core business it makes sense to go to an external partner such as BoatyardX. Discover how this approach works for Toronto-based Global Solutions Team.
We were recently interviewed by a new Software Insider website using a Reporter BOT, and it didn't go great! Sometimes #articialintelligence isn't as smart as we'd expect! See what you think.
Irish technology company BoatyardX delivers a compelling case for moving to the cloud to ensure the viability of your operations for the future.
As a growing start up, it’s important not to lose sight of the security and controls required on the IT systems that underpin the business. See how a recent Pen Test has resulted in significant cost savings at BoatyardX.
Pushing a new product live and then helping to demonstrate to early beta customers is a fantastic experience for a software development team.
BoatyardX’s approach to the cloud uses scalable, flexible Kubernetes technology. For businesses undergoing digital transforming, it is the wisest strategy.
Covid-19 represents both a driver and an opportunity for businesses to use digital innovation and build new products and applications more rapidly.